Home / CAF

CAF
Cloud Adoption Framework
Cloud Adoption Framework (CAF) in practice
When companies decide to move to the cloud, there are many factors to consider, and they are not just about technology and architecture. There are many additional aspects to consider, including cost, security, governance and compliance.
Cloud technologies offer many architecture and solution options, but unfortunately, it is time-consuming for IT departments to conduct costly R&D and enter into a proof-of-concept state. This often goes against the business’ need to accelerate time-to-value and the desire to see fast results or choose the MVP path (minimum viable product). Fortunately, Microsoft has addressed this challenge and launched the Cloud Adoption Framework (CAF), designed to help companies embark on their cloud journey in a speedy and structured way.
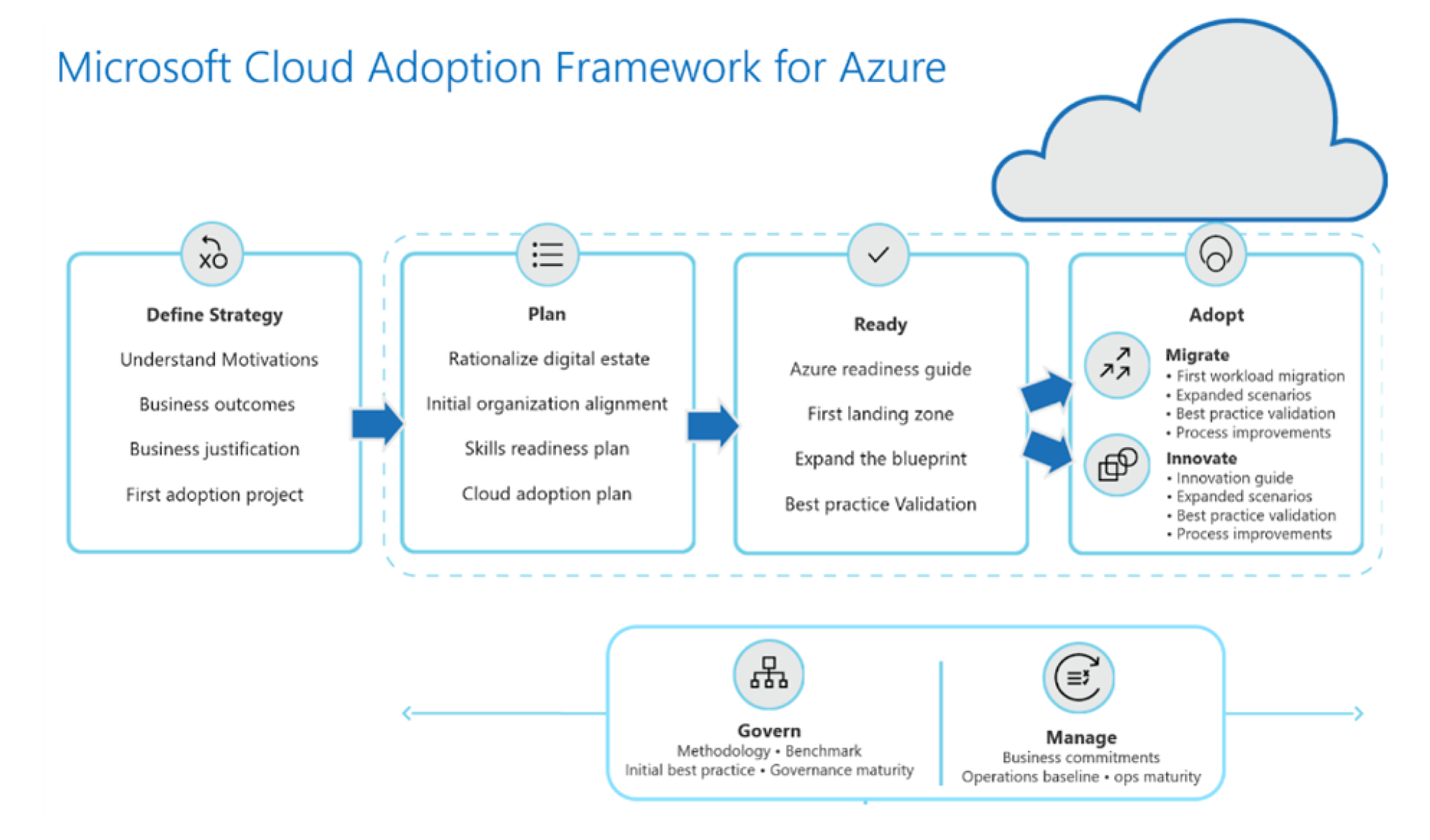
CAF consists of ‘best practice’ documentation, templates, guides and tools that cloud architects, IT professionals and the decision makers can use to achieve the short-term and long-term goals. To further operationalize CAF on the technical side, Microsoft has launched the Enterprise-Scale (2020) – a reference architecture and implementation strategy that facilitates the practical establishment of workloads in Azure by using the landing zone concept.
Enterprise-Scale builds on hands-on experience from a large number of enterprise implementations around the world. Thus you can avoid making the same mistakes as others and can quickly achieve the best solution.
CAF is a well-proven method and at Skaylink we have practical experience in using the framework and utilizing Enterprise-Scale Landing Zone tools to implement wall-to-wall cloud infrastructure and development projects.

PFA gets ready for the future with Azure hybrid cloud infrastructure
CAF and Enterprise-Scale
The more business oriented part of CAF addresses strategy and planning – disciplines that a number of companies have often managed on their own. The challenges are often centred around how to operationalize the cloud platform, in other words: How the “Ready”, “Adopt”, “Govern” and “Manage” phases should be implemented. Concrete guardrails and governance guidelines must be established for how the cloud should be used – who can do what and how. For example: How to develop, what services can be provisioned, how costs are managed, are all security aspects well addressed, etc.
Of course, there is not just one single standard for implementation, but we at Skaylink have solid hands-on experience with the practical implementation of the Enterprise-Scale architecture and Azure landing zones.
Create your cloud environment with Azure landing zones
Azure landing zones are “templates” with policies that go beyond subscriptions and relate to scaling, security, management, networking and identity. Azure landing zones enable application migration and development of large-scale greenfield projects on Azure.
These zones handle all the platform resources needed to support application portfolios and do not distinguish between IaaS or PaaS. A landing zone is an environment for handling workloads defined by code. Aspects such as SecOps, DevOps and NetOps are also addressed.
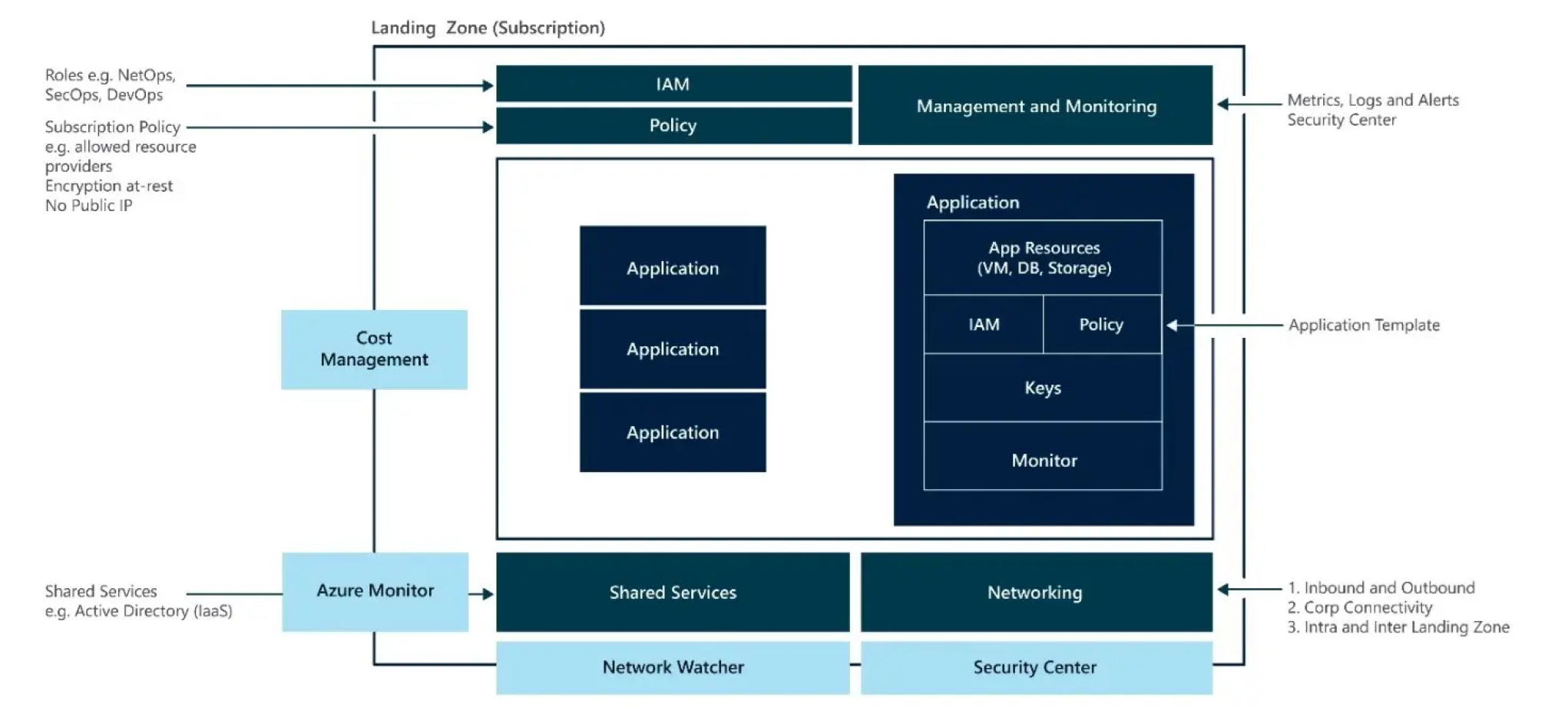
Cloud setup procedure
In practice, we often divide a cloud setup project into the following areas (can be implemented in parallel):
- Cloud governance
- Cloud platform
- Cloud automation
- Cloud security
Cloud governance
- Defines the overall and fundamental guidelines for the cloud environment
- Defines responsibility for risk management, monitoring of Azure Resource Graph and cost management, including reporting and invoicing
- Establishment of governance foundation (Governance MVP) – management groups and subscriptions owner
- Evaluation and implementation of legal aspects, compliance, Azure policies and Azure blueprints
- Defines naming standards (for tags and resources)
- Guidelines for using the cloud platform, PaaS and IaaS, including API Management
Cloud platform
- Defines the basic use of the Azure portal and ensure that it is adequately made available for the individual solutions, without compromising requirements and guidelines for security and governance
- Ensures that environments and resources can be made available quickly and efficiently
- Implements and makes available platform reference architectures
- Prerequisites for SLA requirements, performance, replication, backup and restore/recovery
- Defines and implements the operating and service model, as well as its operational execution
- Ensures efficient operation, administration, monitoring, supervision, logging, App Insights
Cloud automation
- Accelerates development on the cloud platform with full compliance with guidelines
- Establishes automation templates to ensure consistent configuration of Azure resources across solutions and environments
- Collects and shares components that can have common use
- Makes available Azure DevOps for projects, including repositories, build and deploy agents, as well as definitions for build and release pipelines
- Builds the tools for automation in the context of “lighthouse” reference projects
Cloud security
- Defines and evaluates compliance requirements from a security perspective – and ensures that requirements are reflected across
- Defines and implements infrastructure (network, VPN, Bastion/Jumpbox, firewall)
- Defines and implements identity and access
- Prepares guidelines for solution-specific management of users, roles, security groups, MFA and SSO
- Defines encryption requirements (in-transit, at-rest, …)
- Defines and implements Threat Protection, and reports on it
- Defines and implements security requirements between on-premises and cloud
Cloud Security
- Defines and evaluates compliance requirements from a security perspective – and ensures that requirements are reflected across
- Defines and implements infrastructure (network, VPN, Bastion / Jumpbox, firewall)
- Defines and implements identity and access
- Prepares guidelines for solution-specific management of users, roles, security groups, MFA and SSO
- Defines encryption requirements (in-transit, at-rest, …)
- Defines and implements Threat Protection, and reports on it
- Defines and implements security requirements between on-premise and cloud
Can we help you with your cloud journey?
We’re ready to learn about your unique requirements.